A new exploitation method has been discovered for the Linux kernel use-after-free (UAF) vulnerability tracked as CVE-2024-50264. The vulnerability was awarded the Pwnie Award 2025 for Best Privilege […]
Author: cyberbytes
Qualys Confirms Cyberattack Campaign Targeting Salesforce via Salesloft and Drift
Qualys has confirmed that it was recently impacted by a cybersecurity campaign targeting Salesloft and Drift, two third-party SaaS platforms that integrate with Salesforce. The […]
Maduro Hails Huawei Mate X6 Gift From China as ‘Unhackable’ by U.S.
Venezuelan President Nicolás Maduro made bold claims about cybersecurity during a press conference on September 1, 2025, as he showcased a Huawei smartphone gifted to […]
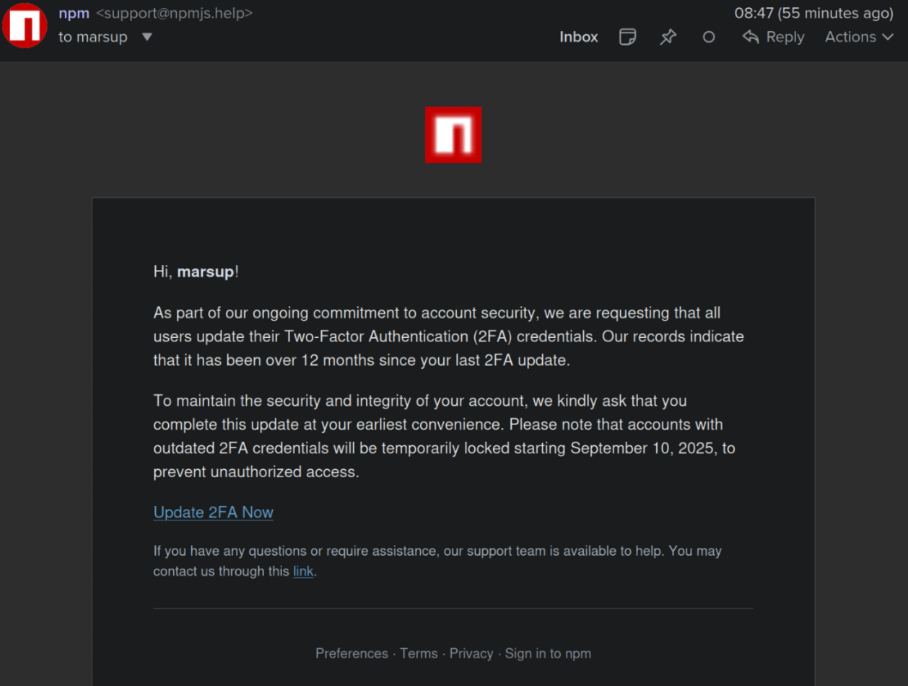
Hackers Hijack 18 Popular npm Packages Downloaded Over 2 Billion Times Weekly
Hackers have hijacked 18 extremely popular npm packages, downloaded more than 2 billion times every week, injecting them with sophisticated malware that targets cryptocurrency users […]
Chinese Hackers Salt Typhoon and UNC4841 Team Up to Breach Critical Infrastructure
Cybersecurity researchers at Silent Push have uncovered a sophisticated Chinese espionage operation linking two prominent threat actors, Salt Typhoon and UNC4841, revealing previously unreported infrastructure […]
45 Previously Unreported Domains Expose Longstanding Salt Typhoon Cyber Espionage
Threat hunters have discovered a set of previously unreported domains, some going back to May 2020, that are associated with China-linked threat actors Salt Typhoon […]
AI powered autonomous ransomware campaigns are coming, say experts
The creation of an AI proof of concept that can autonomously build and execute a ransomware attack from scratch shouldn’t alarm CISOs who are prepared, […]
18 Popular Code Packages Hacked, Rigged to Steal Crypto
At least 18 popular JavaScript code packages that are collectively downloaded more than two billion times each week were briefly compromised with malicious software today, […]
Salesloft Breached via GitHub Account Compromise
The breach kickstarted a massive supply chain attack that led to the compromise of hundreds of Salesforce instances through stolen OAuth tokens. The original article […]
‘MostereRAT’ Malware Blends In, Blocks Security Tools
A threat actor is using a sophisticated EDR-killing malware tool in a campaign to maintain long-term, persistent access on Windows systems. The original article found […]


.webp?ssl=1)