Africa becomes a proving ground for AI-driven phishing, deepfakes, and impersonation, with attackers testing techniques against governments and enterprises.
The original article found on darkreading Read More
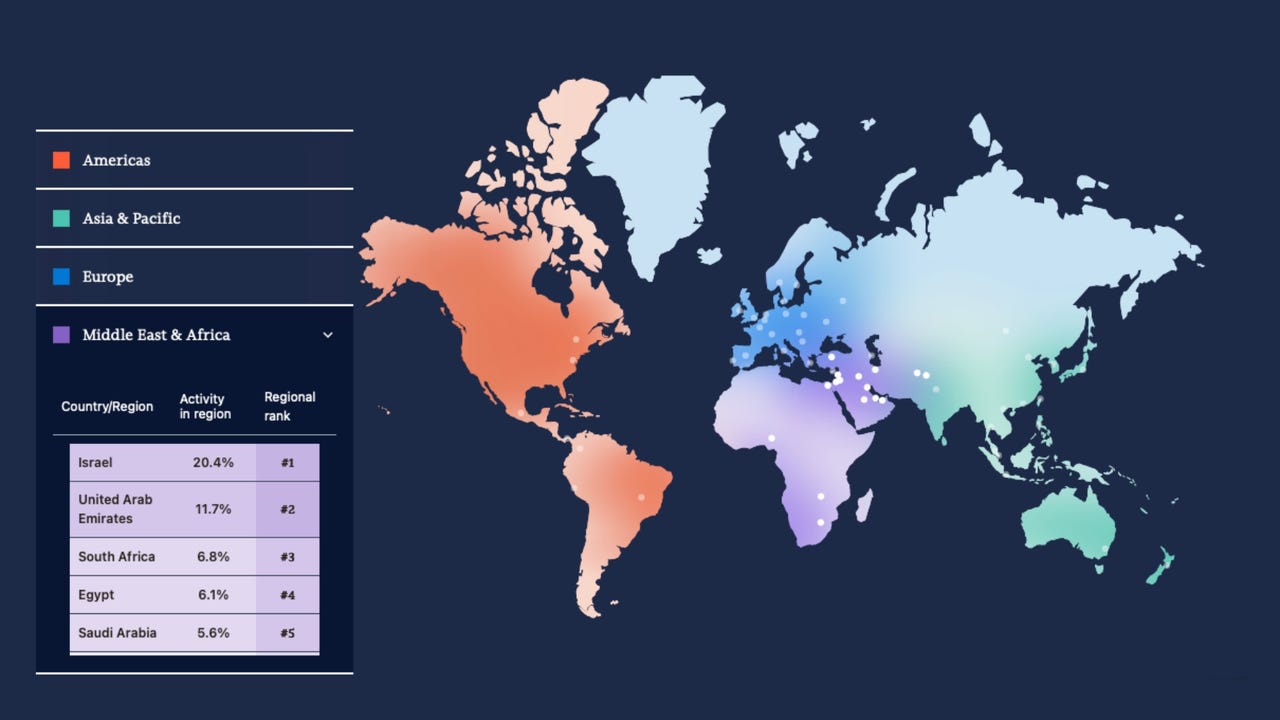
Africa becomes a proving ground for AI-driven phishing, deepfakes, and impersonation, with attackers testing techniques against governments and enterprises.
The original article found on darkreading Read More