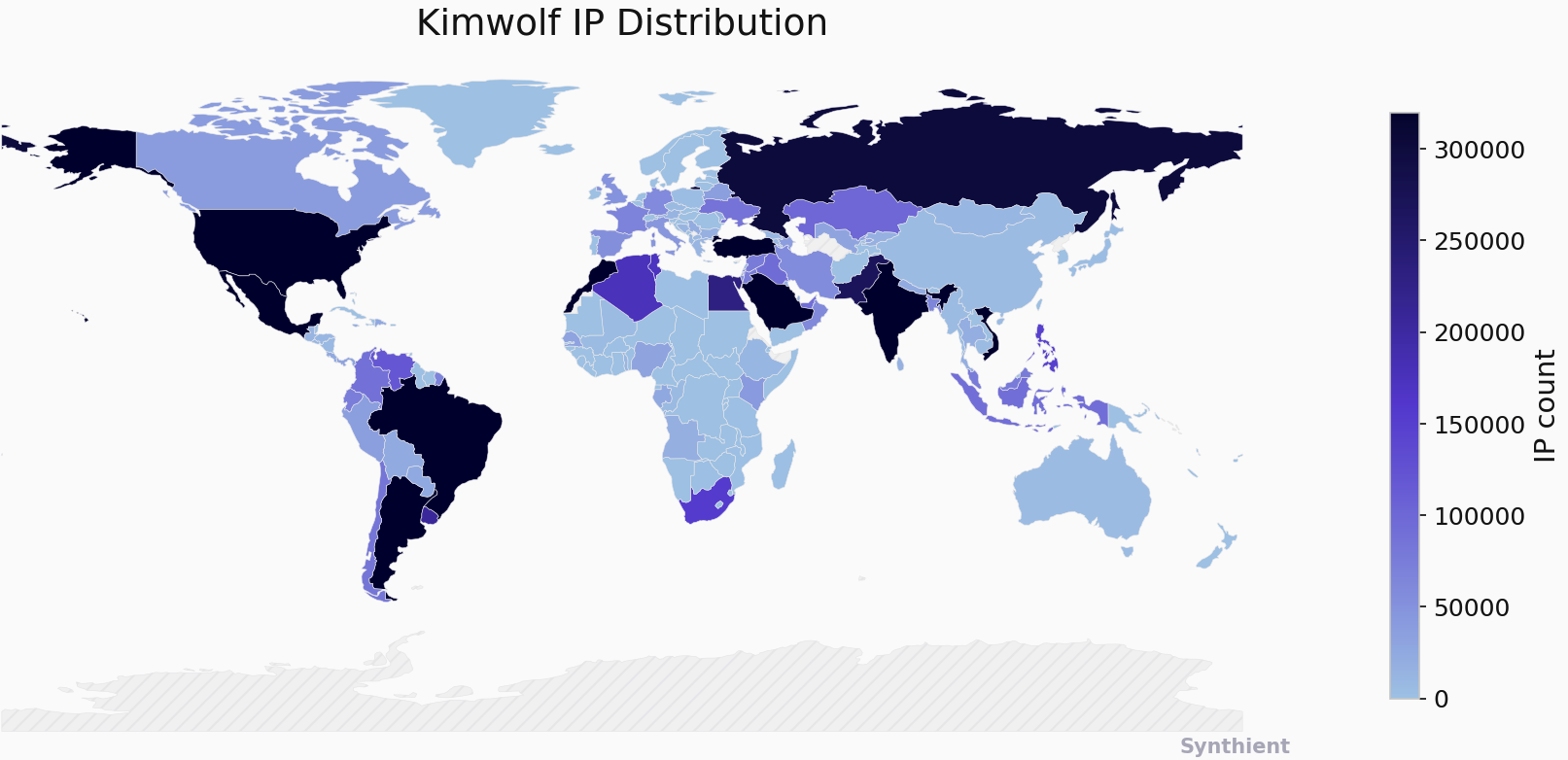
The story you are reading is a series of scoops nestled inside a far more urgent Internet-wide security advisory. The vulnerability at issue has been […]
Google is testing a new image AI and it’s going to be its fastest model
Google is testing a new image AI model called “Nano Banana 2 Flash,” and it’s going to be as good as the Gemini 3 Pro […]
Traditional Security Frameworks Leave Organizations Exposed to AI-Specific Attack Vectors
In December 2024, the popular Ultralytics AI library was compromised, installing malicious code that hijacked system resources for cryptocurrency mining. In August 2025, malicious Nx […]
Top 5 real-world AI security threats revealed in 2025
The year of agentic AI came with promises of massive productivity gains for businesses, but the rush to adopt new tools and services also opened […]
The CSO guide to top security conferences
There is nothing like attending a face-to-face event for career networking and knowledge gathering, and we don’t have to tell you how helpful it can […]
27 Malicious npm Packages Used as Phishing Infrastructure to Steal Login Credentials
Cybersecurity researchers have disclosed details of what has been described as a “sustained and targeted” spear-phishing campaign that has published over two dozen packages to […]
MongoDB Vulnerability CVE-2025-14847 Under Active Exploitation Worldwide
A recently disclosed security vulnerability in MongoDB has come under active exploitation in the wild, with over 87,000 potentially susceptible instances identified across the world. […]
React2Shell: Anatomy of a max-severity flaw that sent shockwaves through the web
The React 19 library for building application interfaces was hit with a remote code vulnerability, React2Shell, about a month ago. However, as researchers delve deeper into the […]
Fortinet warns of 5-year-old FortiOS 2FA bypass still exploited in attacks
Fortinet has warned customers that threat actors are still actively exploiting a critical FortiOS vulnerability that allows them to bypass two-factor authentication (2FA) when targeting […]
Microsoft Copilot is rolling out GPT 5.2 as “Smart Plus” mode
Microsoft is rolling out GPT 5.2 to Copilot on the web, Windows, and mobile as a free upgrade, and it’ll coexist with the GPT 5.1 […]