Austin, TX, USA, December 4th, 2025, CyberNewsWire Phishing has surged 400% year-over-year, highlighting need for real-time visibility into identity exposures. SpyCloud, the leader in identity […]
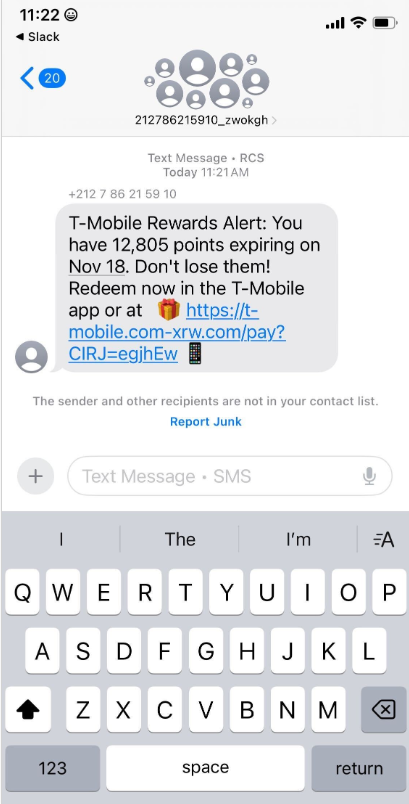
SMS Phishers Pivot to Points, Taxes, Fake Retailers
China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in […]
How Agentic AI Can Boost Cyber Defense
Transurban head of cyber defense Muhammad Ali Paracha shares how his team is automating the triaging and scoring of security threats as part of the […]
Suspicious traffic could be testing CDN evasion, says expert
An individual or group is doing new probing of content delivery networks (CDNs), an effort that CSOs, CIOs and network administrators should worry about if […]
CISA Publishes Security Guidance for Using AI in OT
Global cybersecurity agencies published guidance regarding AI deployments in operational technology, a backbone of critical infrastructure. The original article found on darkreading Read More
CISA Warns of ‘Ongoing’ Brickstorm Backdoor Attacks
State-sponsored actors tied to China continue to target VMware vSphere environments at government and technology organizations. The original article found on darkreading Read More
AI creates new security risks for OT networks, warns NSA
The security of operational technology (OT) in critical infrastructure has been a recurring theme for years, but this week the US National Security Agency (NSA) […]
From feeds to flows: Using a unified linkage model to operationalize threat intelligence
The problem: Static intelligence in a dynamic world Every CISO knows the fatigue that comes with modern threat intelligence. Dozens of vendor feeds pour in […]
Silver Fox Uses Fake Microsoft Teams Installer to Spread ValleyRAT Malware in China
The threat actor known as Silver Fox has been spotted orchestrating a false flag operation to mimic a Russian threat group in attacks targeting organizations […]
ServiceNow’s Acquisition of NHI Provider Veza Strengthens Governance Portfolio
The deal, believed to be valued at $1 billion, will bring non-human identity access control of agents and machines to ServiceNow’s offerings including its new […]

_Dragos_Condrea_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)






_Mohd_Izzuan_Roslan_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)