Mozilla has announced a significant transparency initiative for its Firefox browser ecosystem, implementing mandatory data disclosure requirements for extension developers. Starting November 3rd, 2025, all […]
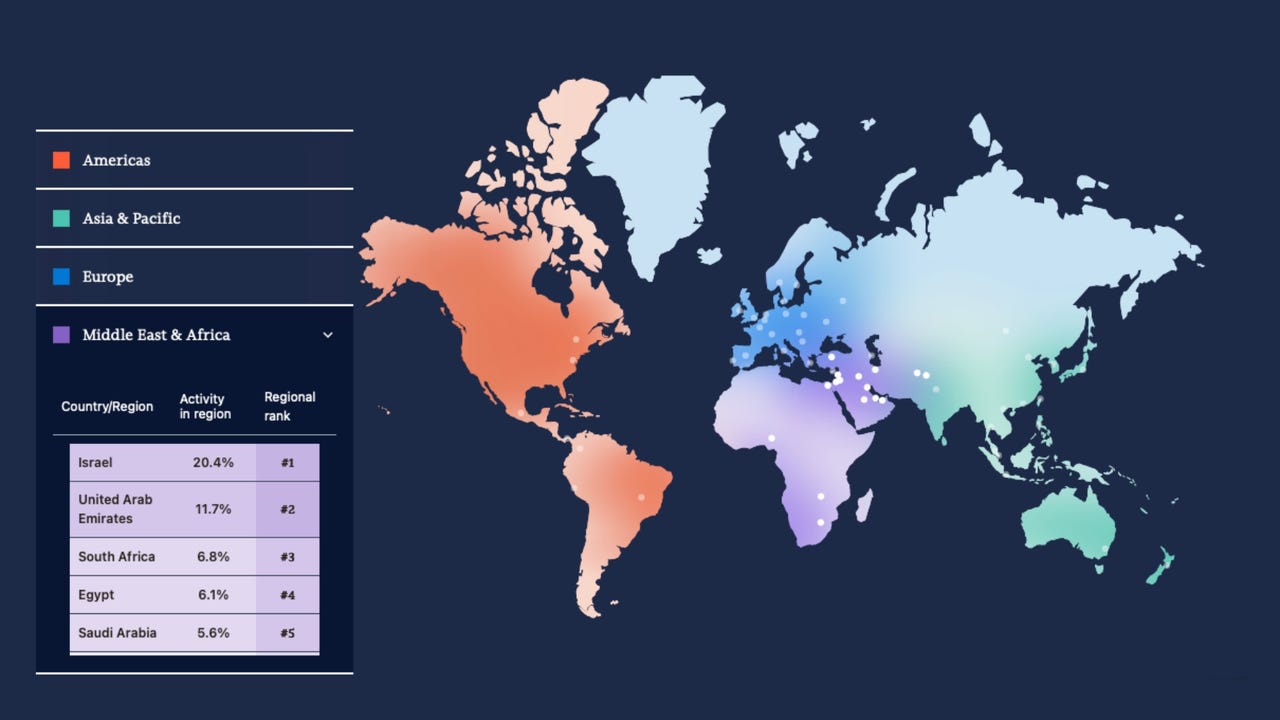
Cybersecurity Firms See Surge in AI-Powered Attacks Across Africa
Africa becomes a proving ground for AI-driven phishing, deepfakes, and impersonation, with attackers testing techniques against governments and enterprises. The original article found on darkreading […]
Software Bill of Material umsetzen: Die besten SBOM-Tools
Nur wenn Sie wissen, was drinsteckt, können Sie sich sicher sein, dass alles mit rechten Dingen zugeht. Das gilt für Fast Food wie für Software. […]
Atroposia malware kit lowers the bar for cybercrime — and raises the stakes for enterprise defenders
Cybercrime is increasingly being commoditized, significantly lowering the bar for hackers and making things tougher for defenders. Researchers at Varonis have discovered a turnkey plug-and-play […]
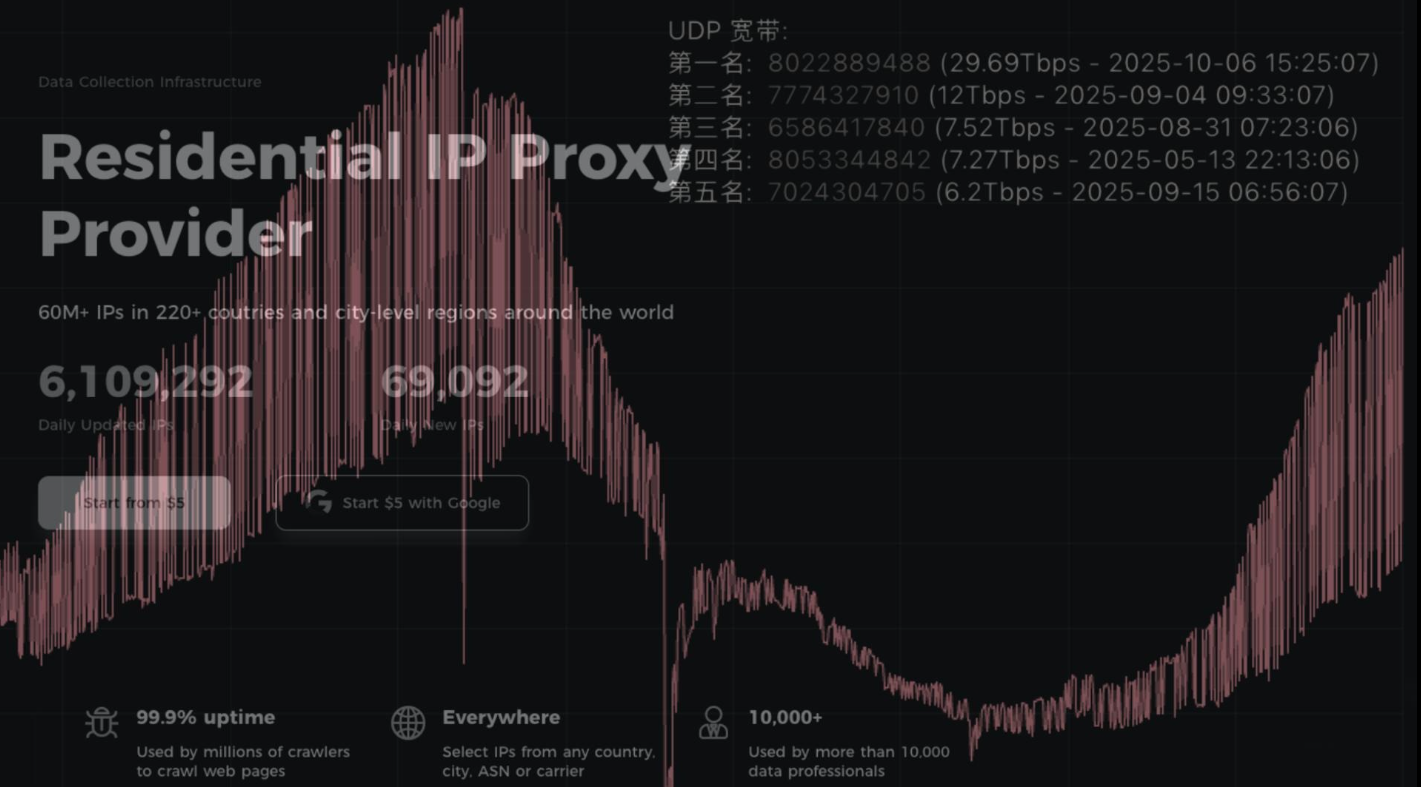
Aisuru Botnet Shifts from DDoS to Residential Proxies
Aisuru, the botnet responsible for a series of record-smashing distributed denial-of-service (DDoS) attacks this year, recently was overhauled to support a more low-key, lucrative and […]
From Chef to CISO: An Empathy-First Approach to Cybersecurity Leadership
Myke Lyons, CISO at data-processing SaaS company Cribl, shares how he cooked up an unconventional journey from culinary school to cybersecurity leadership. The original article […]
Oracle EBS Attack Victims May Be More Numerous Than Expected
Numerous organizations have been attacked via Oracle EBS zero-day CVE-2025-61882, and evidence suggests more like Schneider Electric could be on that list. The original article […]
YouTube Ghost Network Utilizes Spooky Tactics to Target Users
The malware operation uses compromised accounts and bot networks to distribute infostealers and has tripled its output in 2025. The original article found on darkreading […]
Google Chrome to warn users before opening insecure HTTP sites
Google announced today that the Chrome web browser will ask for permission by default before connecting to public, insecure HTTP websites, beginning with Chrome 154 […]
TEE.Fail attack breaks confidential computing on Intel, AMD, NVIDIA CPUs
Academic researchers developed a side-channel attack called TEE.Fail, which allows extracting secrets from the trusted execution environment in the CPU, the highly secure area of a […]