A Chinese-sponsored cyber attack was so damaging that it was briefly proposed that an entire data hub be destroyed, according to British news magazine The […]
North Korean threat actors turn blockchains into malware delivery servers
Nation-state threat actors and cybercriminals are increasingly abusing cryptocurrency blockchains to host malicious payloads with a technique known as “EtherHiding,” which makes their attacks harder […]
Microsoft Disrupts Ransomware Campaign Abusing Azure Certificates
Microsoft revoked more than 200 digital certificates that threat actors used to sign fake Teams binaries that set the stage for Rhysida ransomware attacks. The […]
AI Agent Security: Whose Responsibility Is It?
The shared responsibility model of data security, familiar from cloud deployments, is key to agentic services, but cybersecurity teams and corporate users often struggle with […]
AI Chat Data Is History’s Most Thorough Record of Enterprise Secrets, Secure it Wisely
AI interactions are becoming one of the most revealing records of human thinking; and we’re only beginning to understand what that means for law enforcement, […]
North Korean Hackers Combine BeaverTail and OtterCookie into Advanced JS Malware
The North Korean threat actor linked to the Contagious Interview campaign has been observed merging some of the functionality of two of its malware programs, […]
TikTok Videos Weaponized to Deliver Self-Compiling PowerShell Malware
Attackers are exploiting TikTok’s massive reach to trick users into executing malware through seemingly innocuous videos. In one popular TikTok video (liked over 500 times), […]
WatchGuard VPN Flaw Allows Remote Attackers to Execute Arbitrary Code
A critical security vulnerability has been discovered in WatchGuard Firebox appliances that could allow remote attackers to execute arbitrary code without authentication. The flaw, identified […]
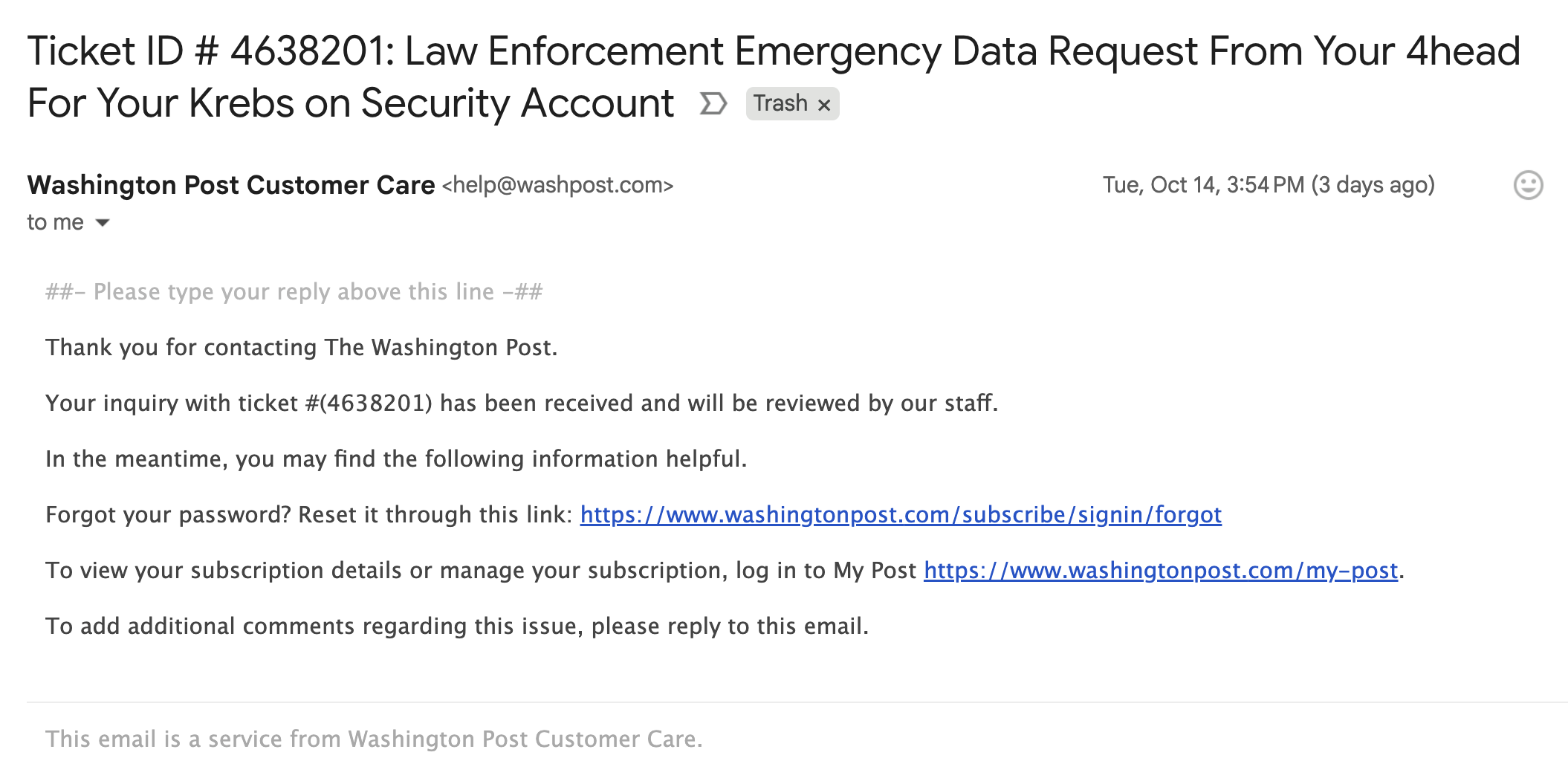
Attackers Exploit Zendesk Authentication Issue to Flood Targets’ Inboxes with Corporate Notifications
Cybercriminals have discovered a gap in Zendesk’s ticket submission process and are using it to bombard victims with waves of misleading support messages. When configured […]
Email Bombs Exploit Lax Authentication in Zendesk
Cybercriminals are abusing a widespread lack of authentication in the customer service platform Zendesk to flood targeted email inboxes with menacing messages that come from […]