Microsoft previewed the Sentinel security graph and MCP server at its annual Microsoft Secure virtual event earlier this month. The original article found on darkreading […]
Chinese Hackers Use Velociraptor IR Tool in Ransomware Attacks
In a new wrinkle for adversary tactics, the Storm-2603 threat group is abusing the digital forensics and incident response (DFIR) tool to gain persistent access […]
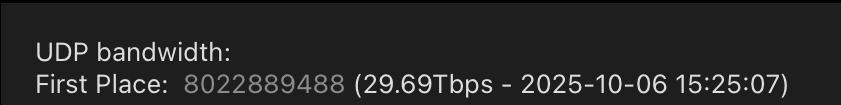
DDoS Botnet Aisuru Blankets US ISPs in Record DDoS
The world’s largest and most disruptive botnet is now drawing a majority of its firepower from compromised Internet-of-Things (IoT) devices hosted on U.S. Internet providers […]
Feds Shutter ShinyHunters Salesforce Extortion Site
The group warned that law-enforcement crackdowns are imminent in the wake of the takedown, but its extortion threats against Salesforce victims remain active. The original […]
SonicWall data breach affects all cloud backup customers
On Sept. 17, security vendor SonicWall announced that cybercriminals had stolen backup files configured for cloud backup. At the time, the company claimed the incident was […]
Microsoft Warns of ‘Payroll Pirates’ Hijacking HR SaaS Accounts to Steal Employee Salaries
A threat actor known as Storm-2657 has been observed hijacking employee accounts with the end goal of diverting salary payments to attacker-controlled accounts. “Storm-2657 is […]
Nanoprecise partners with AccuKnox to strengthen its Zero Trust Cloud Security and Compliance Posture
Menlo Park, USA, October 10th, 2025, CyberNewsWire AccuKnox, a leader in Zero Trust Cloud Native Application Protection Platforms (CNAPP), is proud to announce that Nanoprecise […]
Stealit Malware Abuses Node.js Single Executable Feature via Game and VPN Installers
Cybersecurity researchers have disclosed details of an active malware campaign called Stealit that has leveraged Node.js’ Single Executable Application (SEA) feature as a way to […]
Deepfake Awareness High at Orgs, But Cyber Defenses Badly Lag
The vast majority of organizations are encountering AI-augmented threats, but remain confident in their defenses, despite inadequate detection investment and more than half falling to […]
How Important are Accessible Website Designs in 2025?
In 2025, the importance of a top-quality and well-functioning website cannot be overstated. Forgetting this is a costly mistake, but an even greater one is […]
_Mopic_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)