Phishing has surged 400% year-over-year, highlighting need for real-time visibility into identity exposures. SpyCloud, the leader in identity threat protection, today released new data showing […]
15 years in, zero trust remains elusive — with AI rising to complicate the challenge
The zero trust approach cybersecurity access control is more than 15 years old but organizations continue to struggle with its implementation due in large part […]
Coupang breach of 33.7 million accounts allegedly involved engineer insider
A prolonged lack of management of valid authentication keys for signed access tokens issued to authenticators is believed to be the root cause of over […]
Das CISO-Paradoxon: Innovation ermöglichen und Risiken managen
CISOs sollten eng mit anderen Teams zusammenarbeiten. eamesBot – shutterstock.com Eine der Hauptaufgaben von CISOs besteht darin, nicht mehr die „Abteilung des Neins“ zu sein. […]
SpyCloud Data Shows Corporate Users 3x More Likely to Be Targeted by Phishing Than by Malware
Austin, TX, USA, December 4th, 2025, CyberNewsWire Phishing has surged 400% year-over-year, highlighting need for real-time visibility into identity exposures. SpyCloud, the leader in identity […]
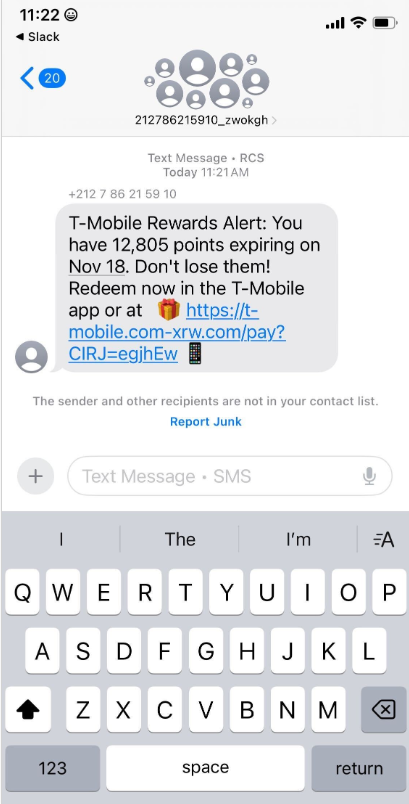
SMS Phishers Pivot to Points, Taxes, Fake Retailers
China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in […]
How Agentic AI Can Boost Cyber Defense
Transurban head of cyber defense Muhammad Ali Paracha shares how his team is automating the triaging and scoring of security threats as part of the […]
Suspicious traffic could be testing CDN evasion, says expert
An individual or group is doing new probing of content delivery networks (CDNs), an effort that CSOs, CIOs and network administrators should worry about if […]
CISA Publishes Security Guidance for Using AI in OT
Global cybersecurity agencies published guidance regarding AI deployments in operational technology, a backbone of critical infrastructure. The original article found on darkreading Read More
CISA Warns of ‘Ongoing’ Brickstorm Backdoor Attacks
State-sponsored actors tied to China continue to target VMware vSphere environments at government and technology organizations. The original article found on darkreading Read More





_Dragos_Condrea_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)


