Russian state-sponsored hackers have developed a sophisticated new backdoor malware called “NotDoor” that specifically targets Microsoft Outlook users, enabling attackers to steal sensitive data and […]
TLS Certificate Mis-Issuance Exposes 1.1.1.1 DNS Service to Exploitation
Security researchers revealed that three unauthorized TLS certificates were issued in May 2025 for 1.1.1.1, the widely used public DNS service run by Cloudflare and […]
New Scam Targets PayPal Users During Account Profile Setup
A highly sophisticated phishing campaign is targeting PayPal users with a deceptive email designed to grant scammers direct access to their accounts. The attack, which […]
Iran MOIS Phishes 50+ Embassies, Ministries, Int’l Orgs
The Homeland Justice APT tried spying on countries and organizations from six continents, using more than 100 hijacked email accounts. The original article found on […]
Japan, South Korea Take Aim at North Korean IT Worker Scam
With the continued success of North Korea’s IT worker scams, Asia-Pacific nations are working with private firms to blunt the scheme’s effectiveness. The original article […]
Malicious npm Packages Exploit Ethereum Smart Contracts to Target Crypto Developers
Cybersecurity researchers have discovered two new malicious packages on the npm registry that make use of smart contracts for the Ethereum blockchain to carry out […]
Cloudflare Holds Back the Tide on 11.5Tbps DDoS Attack
It’s the equivalent of watching more than 9,350 full-length HD movies or streaming 7,480 hours of high-def video nonstop in less than a minute. The […]
Russia’s APT28 Targets Microsoft Outlook With ‘NotDoor’ Malware
The notorious Russian state-sponsored hacking unit, also known as Fancy Bear, is abusing Microsoft Outlook for covert data exfiltration. The original article found on darkreading […]
Malicious npm packages use Ethereum blockchain for malware delivery
Attackers behind a recent supply chain attack that involved rogue GitHub repositories and npm packages used smart contracts on the Ethereum blockchain to deliver malware […]
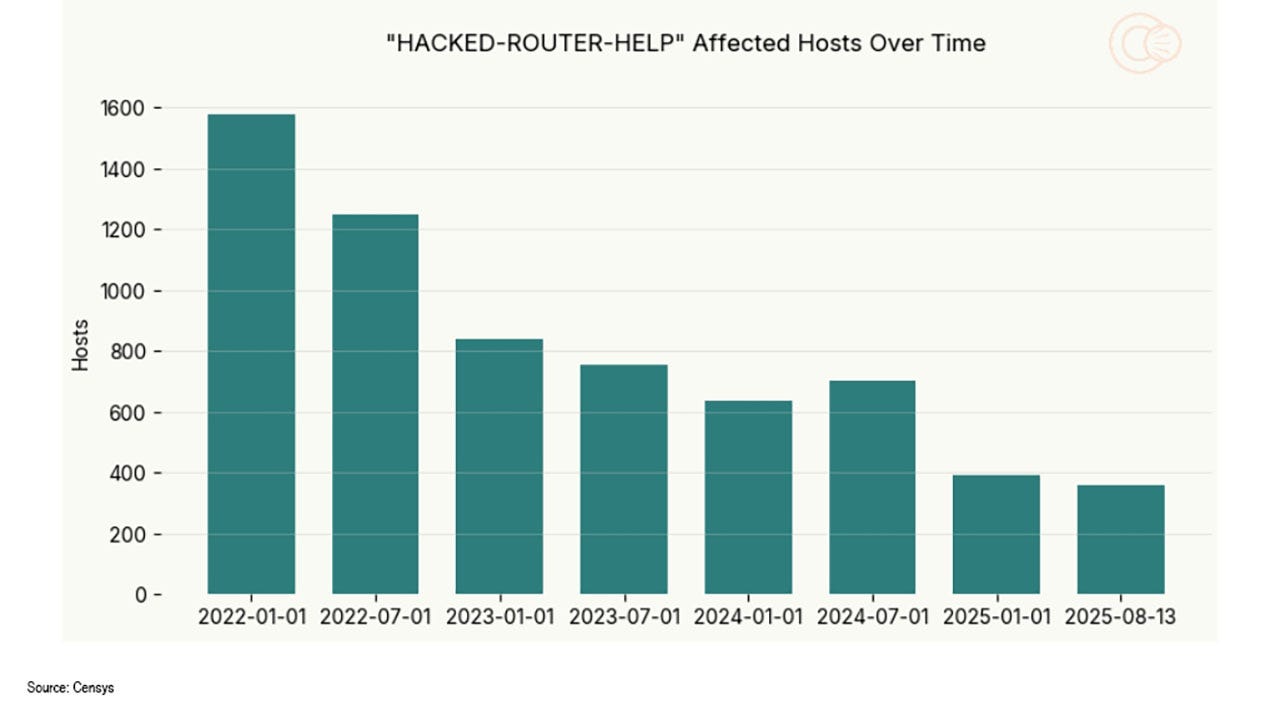
Hacked Routers Linger on the Internet for Years, Data Shows
While trawling Internet scan data for signs of compromised infrastructure, researchers found that asset owners may not know for years their devices had been hacked. […]