Government intelligence and cybersecurity agencies from 13 countries have released a joint advisory detailing the techniques used by Salt Typhoon, a Chinese state-sponsored APT group […]
CISA, FBI, NSA Warn of Chinese ‘Global Espionage System’
Three federal agencies were parties to a global security advisory this week warning about the extensive threat posed by Chinese nation-state actors targeting network devices. […]
1,000+ Devs Lose Their Secrets to an AI-Powered Stealer
One of the most sophisticated supply chain attacks to date caused immense amounts of data to leak to the Web in a matter of hours. […]
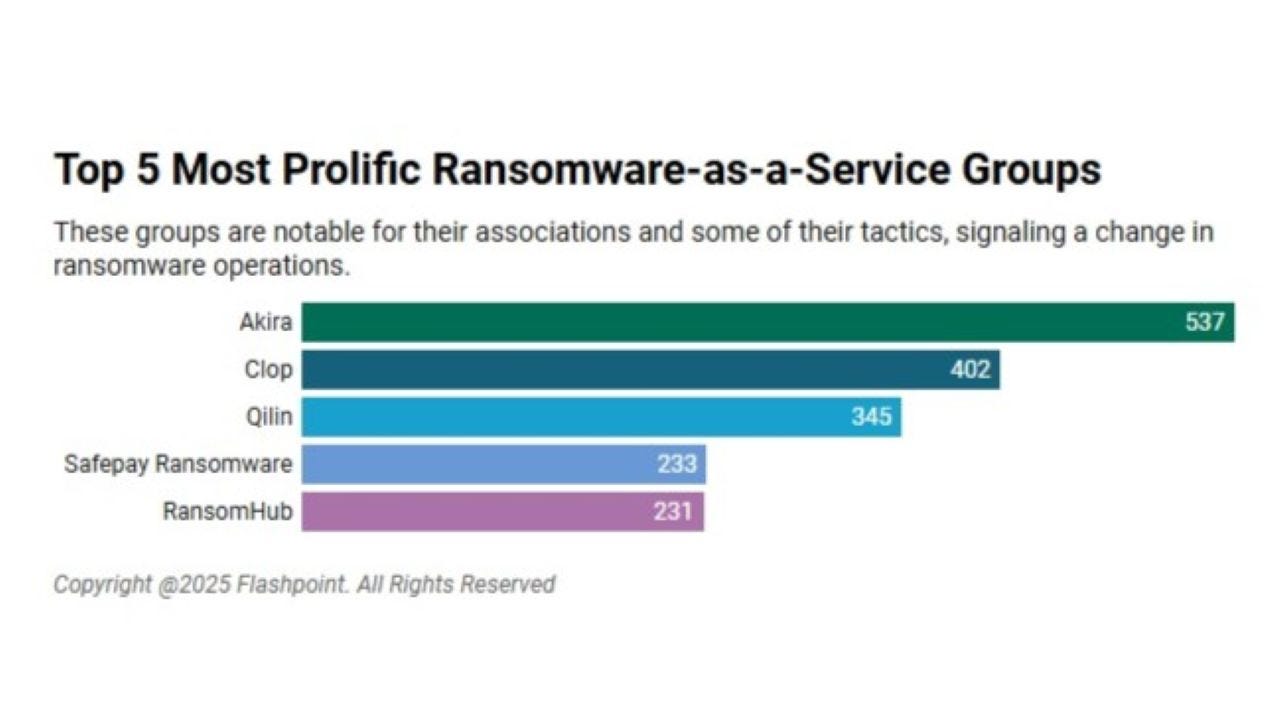
Akira, Cl0p Top List of 5 Most Active Ransomware-as-a-Service Groups
Flashpoint published its 2025 midyear ransomware report that highlighted the top five most prolific groups currently in operation. The original article found on darkreading Read […]
2025 CSO Hall of Fame: George Finney on decryption risks, AI, and the CISO’s growing clout
With more than 20 years of experience at startups, nonprofits, and large universities, George Finney has built a reputation for seeing both the big picture […]
How Gainesville Regional Utilities is locking down vendor risk
Gainesville Regional Utilities (GRU) isn’t just a utilities provider—it’s the communications backbone for the community. In addition to delivering electricity and water, GRU operates fiber-optic […]
Hackers Steal 4M+ TransUnion Customers’ Data
The credit reporting agency said the breach was “limited to specific data elements” and didn’t include credit reports or core credit information. The original article […]
CrowdStrike buys Onum in agentic SOC push
CrowdStrike has announced the purchase of Spanish data intelligence company Onum, which specializes in real-time telemetry pipeline management. According to Fortune, the deal is valued […]
Researchers Find VS Code Flaw Allowing Attackers to Republish Deleted Extensions Under Same Names
Cybersecurity researchers have discovered a loophole in the Visual Studio Code Marketplace that allows threat actors to reuse names of previously removed extensions. Software supply […]
Dark Reading Confidential: A Guided Tour of Today’s Dark Web
Dark Reading Confidential Episode 9: Join us for a look around today’s Dark Web, and find out how law enforcement, AI, nation-state activities, and more […]