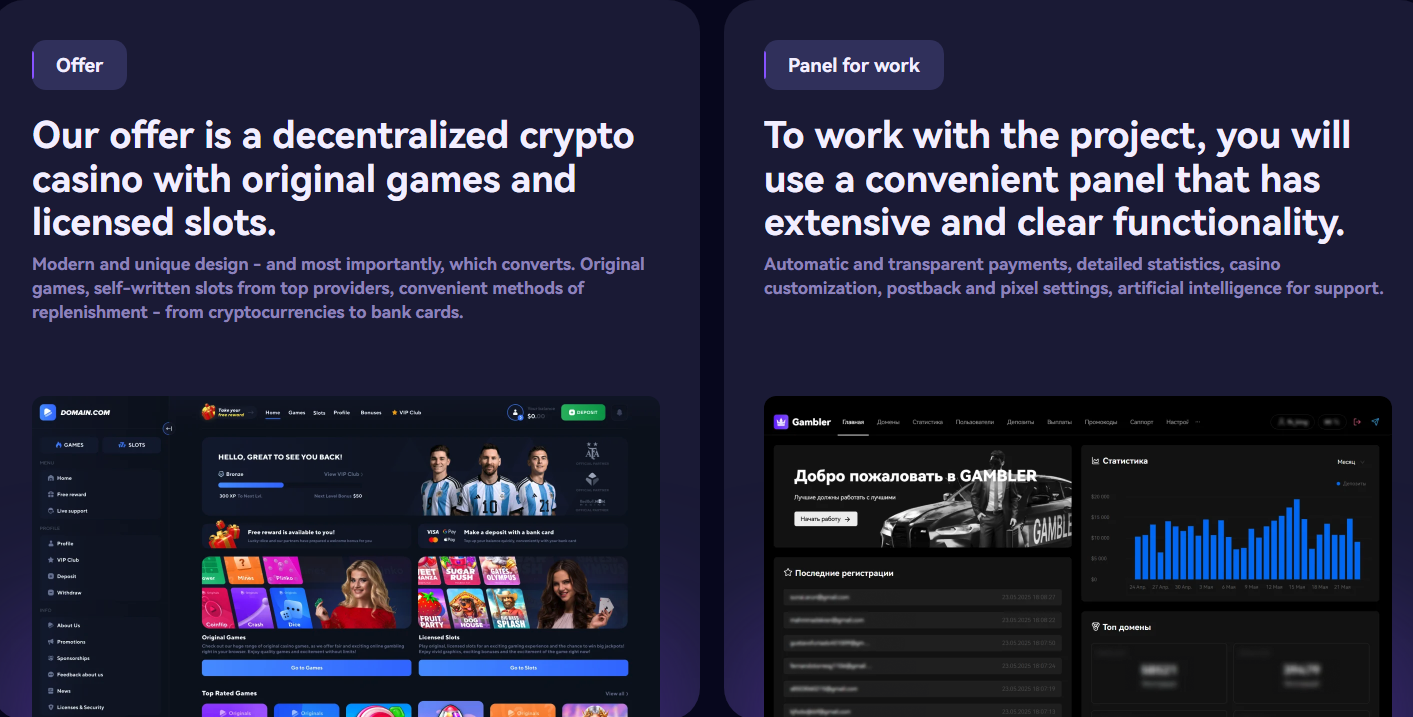
Last month, KrebsOnSecurity tracked the sudden emergence of hundreds of polished online gaming and wagering websites that lure people with free credits and eventually abscond […]
How SafeLine WAF Turns Hackers’ Scanners into Trash
When web application protection is no longer a million-dollar luxury, and when every developer can build their own security perimeter with just a few clicks—that […]
State of Nevada Faces IT Outage Amid Cyberattack, Offices Suspended
The State of Nevada became the target of a significant cyberattack which resulted in a substantial network security incident impacting government infrastructure across multiple agencies. […]
Wave of npm supply chain attacks exposes thousands of enterprise developer credentials
Attacks on the NX build system and React packages highlight escalating threats to enterprise software development pipelines. The original article found on Wave of npm […]
Cisco IMC Virtual Keyboard Vulnerability Allows Attackers to Redirect Users to Malicious Websites
Cisco has released urgent security updates to remediate a high-severity vulnerability in its Integrated Management Controller (IMC) virtual keyboard video monitor (vKVM) module that could […]
Cisco UCS Manager Software Flaw Allows Attackers to Inject Malicious Commands
Cisco has released urgent security updates to remediate two medium-severity command injection vulnerabilities in its UCS Manager Software that could allow authenticated administrators to execute […]
CISA’s New SBOM Guidelines Get Mixed Reviews
Updated SBOM rules from CISA are a solid step toward making them more useful for cyber defenders but don’t address many critical needs, experts say. […]
Electronics Manufacturer Data I/O Suffers Ransomware Breach
Data I/O Corporation, a well-known electronics firm that specializes in device programming and security provisioning solutions, revealed a ransomware attack that penetrated its internal IT […]
Threat Actors Exploit Velociraptor Incident Response Tool for Remote Access
Researchers from the Counter Threat Unit (CTU) at Sophos uncovered a sophisticated intrusion where threat actors repurposed the legitimate open-source Velociraptor digital forensics and incident […]
Salt Typhoon Exploits Cisco, Ivanti, Palo Alto Flaws to Breach 600 Organizations Worldwide
The China-linked advanced persistent threat (APT) actor known as Salt Typhoon has continued its attacks targeting networks across the world, including organizations in the telecommunications, […]



.webp)




