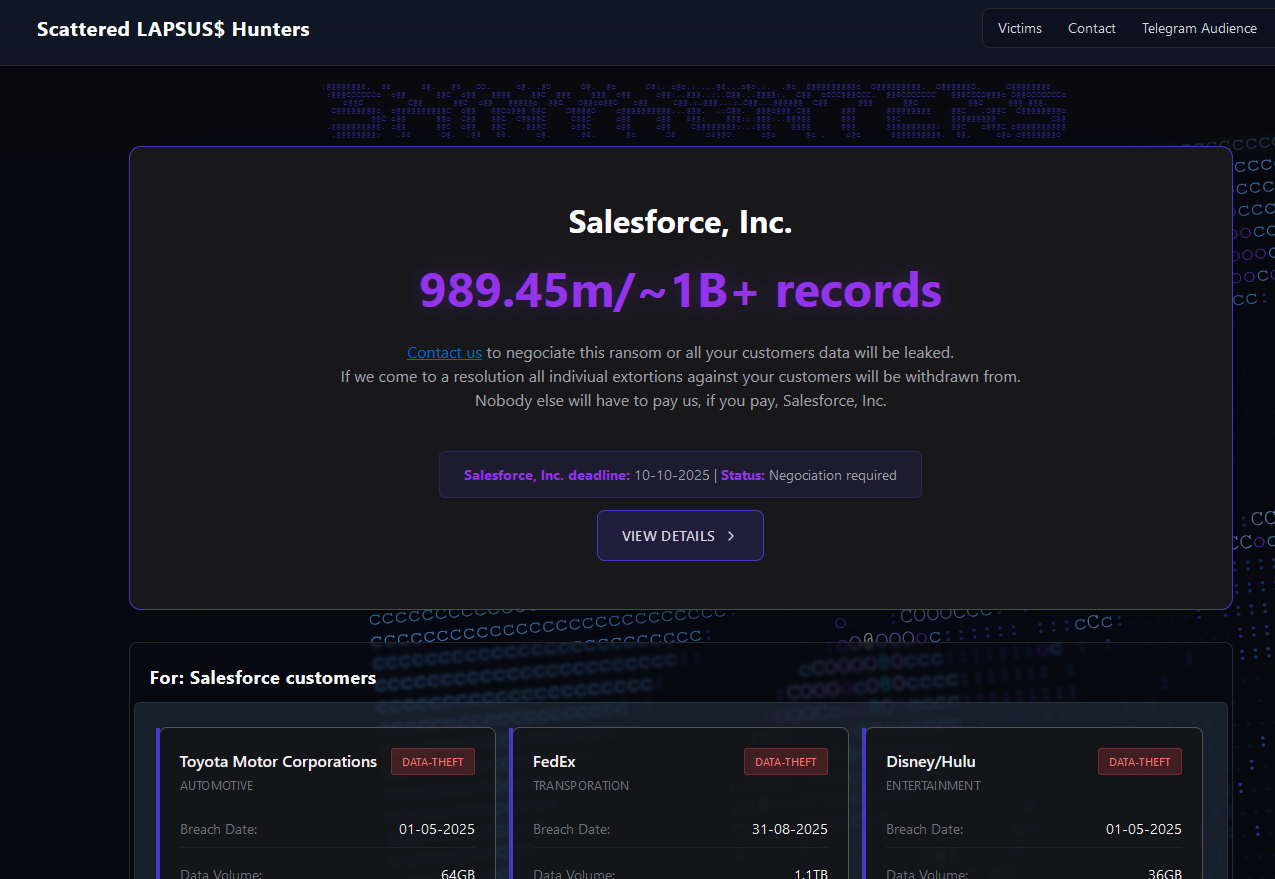
A prolific cybercriminal group that calls itself “Scattered LAPSUS$ Hunters” has dominated headlines this year by regularly stealing data from and publicly mass extorting dozens […]
Qilin Ransomware Turns South Korean MSP Breach Into 28-Victim ‘Korean Leaks’ Data Heist
South Korea’s financial sector has been targeted by what has been described as a sophisticated supply chain attack that led to the deployment of Qilin […]
Prompt Injections Loom Large Over ChatGPT’s Atlas Browser
It’s the law of unintended consequences: equipping browsers with agentic AI opens the door to an exponential volume of prompt injections. The original article found […]
Chrome Extension Malware Secretly Adds Hidden SOL Fees to Solana Swap Transactions
Security researchers at Socket have uncovered a deceptive Chrome extension called Crypto Copilot that masquerades as a legitimate Solana trading tool while secretly siphoning SOL […]
Neue ClickFix-Kampagne nutzt Fake-Windows-Updates
Cyberkriminelle nutzen eine gefälschte Windows-Update-Seite, um Mitarbeiter anzugreifen. PixieMe / Shutterstock Forscher des Security-Anbieters Huntress sind kürzlich auf eine neue ClickFix-Kampagne gestoßen, die auf Mitarbeiter […]
Enterprises Aren’t Confident They Can Secure Non-Human Identities (NHIs)
More than half of organizations surveyed aren’t sure they can secure non-human identities (NHIs), underscoring the lag between the rollout of these identities and the […]
Hackers Launch Active Attacks on Telecom and Media Industries
The telecommunications & media sector stands at the epicenter of a relentless cyber onslaught, as evidenced by CYFIRMA’s latest quarterly industry report. Leveraging telemetry-driven intelligence […]
Threat Actors Use Fake Update Lures to Deploy SocGholish Malware
In a significant escalation of cyber threats, Arctic Wolf Labs has identified a coordinated campaign in which the Russian-aligned RomCom threat group leverages the SocGholish […]
Massive Data Leak: ByteToBreach Offers Stolen Global Airline, Banking, and Government Records
A cybercriminal operating under the alias ByteToBreach has emerged as a prominent figure in the underground data trade, orchestrating a series of high-profile breaches targeting […]
Developers Are Exposing Passwords and API Keys Through Online Code Tools
Security researchers at watchTowr Labs uncovered a massive leak of sensitive credentials after scanning popular online JSON formatting tools. Developers and administrators have been pasting […]




_2023.png?width=1280&auto=webp&quality=80&disable=upscale)



