In a breakthrough that challenges the perceived safety of nonce-based Content Security Policy (CSP), security researchers have demonstrated a practical method to bypass these protections […]
Cybersecurity in the supply chain: strategies for managing fourth-party risks
Fourth-party vendors have become a serious supply chain cybersecurity blind spot. Unlike third parties with direct contractual relationships, fourth parties — the suppliers your vendors […]
Security-KPIs und -KRIs: So messen Sie Cybersicherheit
Cybersicherheit zu messen, ist kein Kinderspiel. Foto: Ultraskrip – shutterstock.com Eine wichtige Säule jedes ausgereiften Cyberrisk-Programms ist die Fähigkeit, die Performance der IT-Security und registrierte […]
Hunters International shuts ransomware operations, reportedly becomes an extortion-only gang
Ransomware gang Hunters International says it’s shutting down its operations for unexplained reasons, and is offering decryption keys to victim organizations. The offer of decryption […]
Massive Android Fraud Operations Uncovered: IconAds, Kaleidoscope, SMS Malware, NFC Scams
A mobile ad fraud operation dubbed IconAds that consisted of 352 Android apps has been disrupted, according to a new report from HUMAN. The identified […]
Big Tech’s Mixed Response to U.S. Treasury Sanctions
In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of virtual currency investment scam websites […]
New Hpingbot Exploits Pastebin for Payload Delivery and Uses Hping3 for DDoS Attacks
NSFOCUS Fuying Lab’s Global Threat Hunting System has discovered a new botnet family called “hpingbot” that has been quickly expanding since June 2025, marking a […]
Beware of Fake Chinese E-Commerce Sites Imitating Apple, Wrangler, and Exploiting Payment Services like MasterCard and PayPal
A sophisticated phishing campaign, initially spotlighted by Mexican journalist Ignacio Gómez Villaseñor, has evolved into a sprawling global threat, as revealed by Silent Push Threat […]
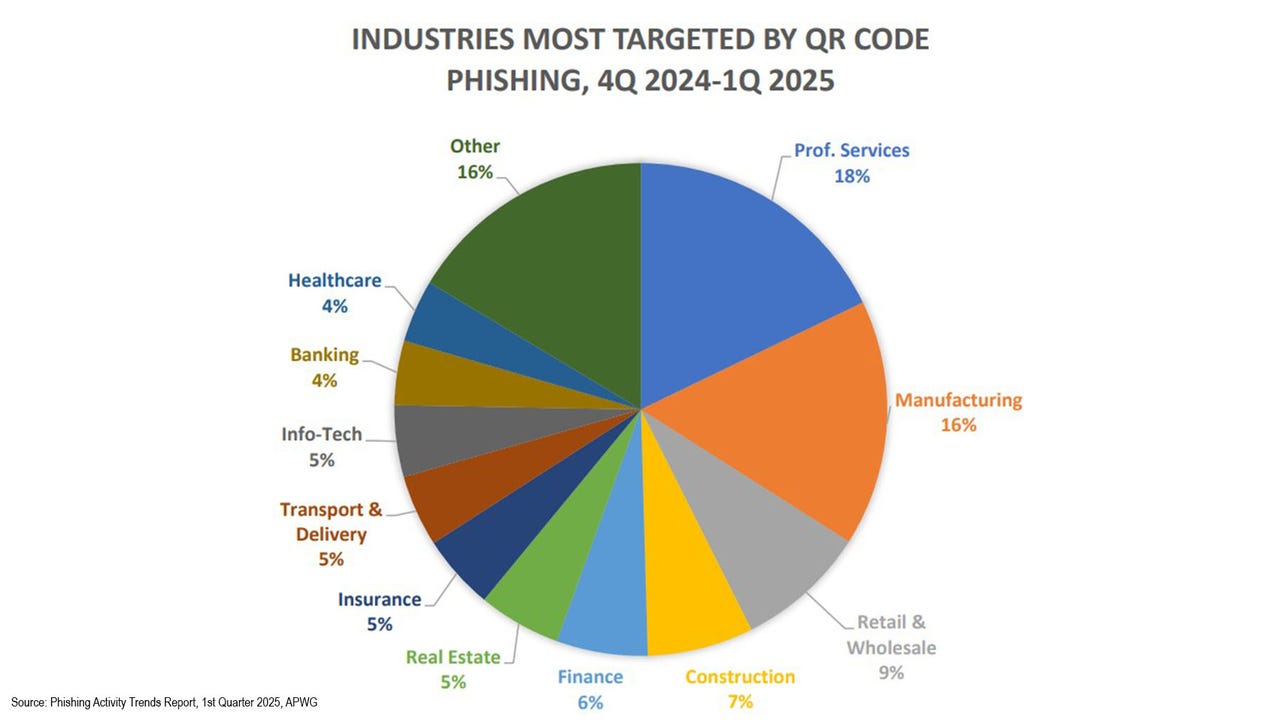
Criminals Sending QR Codes in Phishing, Malware Campaigns
The Anti-Phishing Working Group observed how attackers are increasingly abusing QR codes to conduct phishing attacks or to trick users into downloading malware. The original […]
Citrix Alerts on Authentication Failures After NetScaler Update to Resolve Auth Vulnerability
Citrix has issued an urgent advisory for NetScaler users following the release of builds 14.1.47.46 and 13.1.59.19, warning of potential authentication disruptions stemming from a […]