SolarWinds has released an urgent security update for its Serv-U file transfer software, patching three critical vulnerabilities that could enable attackers with administrative access to […]
New npm Malware Campaign Checks If Visitor Is a Victim or Researcher Before Initiating Infection
The Socket Threat Research Team has uncovered a sophisticated npm malware campaign orchestrated by the threat actor dino_reborn, who deployed 7 malicious packages designed to […]
New FortiWeb 0-Day Code Execution Flaw Actively Exploited
Fortinet has disclosed a critical OS command injection vulnerability affecting multiple versions of FortiWeb that is currently being exploited in the wild. The flaw, tracked […]
New ShadowRay Exploit Targets Vulnerability in Ray AI Framework to Attack AI Systems
Oligo Security researchers have uncovered an active global hacking campaign that leverages artificial intelligence to attack AI infrastructure. The operation, dubbed ShadowRay 2.0, exploits a […]
Behind the firewall: The hidden struggles of cyber professionals with a disability
Problem-solving is what cyber professionals do best, but one problem the industry has yet to solve is inclusion. Despite progress in diversity, research shows many […]
Fortinet Warns of New FortiWeb CVE-2025-58034 Vulnerability Exploited in the Wild
Fortinet has warned of a new security flaw in FortiWeb that it said has been exploited in the wild. The medium-severity vulnerability, tracked as CVE-2025-58034, […]
Anthropic AI-powered cyberattack causes a stir
AI company Anthropic recently announced that companies worldwide have been attacked by an AI-powered cyber espionage campaign. It is purported to be the first publicly […]
Iran-Nexus Threat Actor UNC1549 Takes Aim at Aerospace
Researchers say Israel remains a central focus, with UNC1549 targeting aerospace and defense entities in the US, the UAE, Qatar, Spain, and Saudi Arabia. The […]
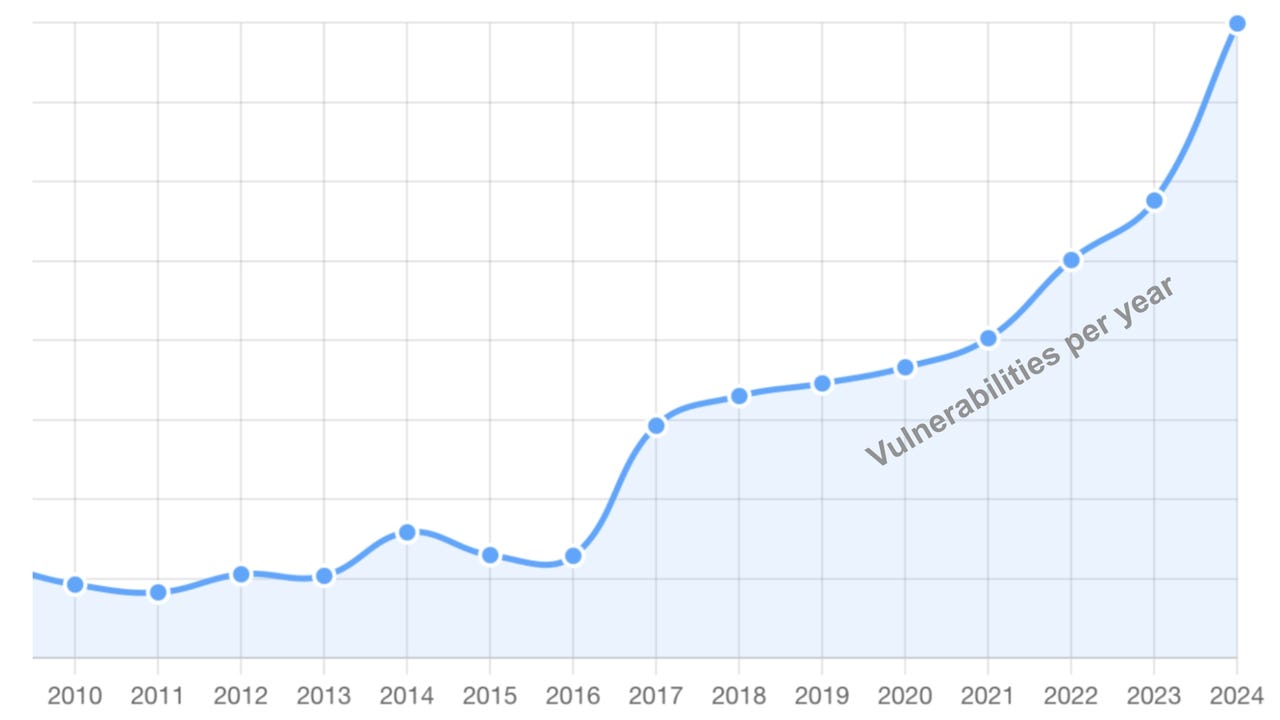
Can a Global, Decentralized System Save CVE Data?
As vulnerabilities in the Common Vulnerabilities and Exposures ecosystem pile up, one Black Hat Europe presenter hopes for a global, distributed alternative. The original article […]
Cloud Break: IoT Devices Open to Silent Takeover Via Firewalls
IoT devices can be compromised, thanks to gaps in cloud management interfaces for firewalls and routers, even if they’re protected by security software or not […]