WhatsApp has introduced an extra layer of privacy called Advanced Chat Privacy that allows users to block participants from sharing the contents of a conversation […]
‘Industrial-Scale’ Asian Scam Centers Expand Globally
The convergence of cybercrime, financial fraud, and organized crime poses a significant threat, especially where these syndicates excel at operating under the radar. The original […]
Ransomware Gangs Innovate With New Affiliate Models
Secureworks research shows two ransomware operators offering multiple business models with ransomware-as-a-service, mimicking the structures and processes of legitimate businesses. The original article found on […]
Microsoft Claims Steady Progress Revamping Security Culture
In the latest Secure Future Initiative Progress Report, Microsoft described efforts to rebuild its security culture, including making security a core priority for employees during […]
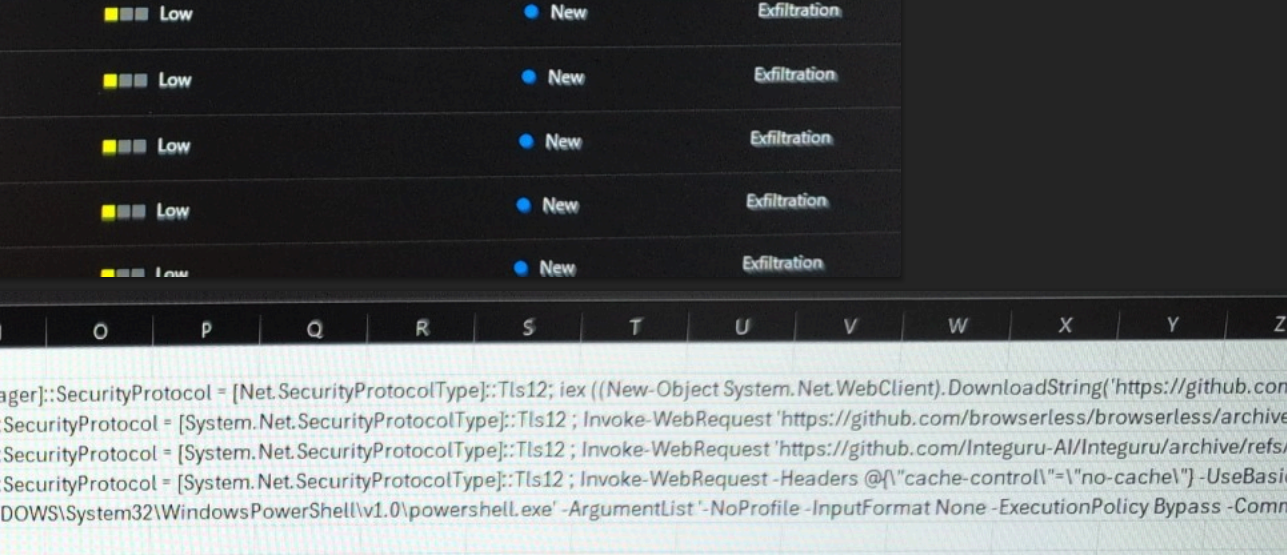
DOGE Worker’s Code Supports NLRB Whistleblower
A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government Efficiency (DOGE) siphoned gigabytes of […]
North Korean Operatives Use Deepfakes in IT Job Interviews
Use of synthetic identities by malicious employment candidates is yet another way state-sponsored actors are trying to game the hiring process and infiltrate Western organizations. […]
Popular British Retailer Marks & Spencer Addresses ‘Cyber Incident’
M&S has launched an investigation and said some customer operations are impacted. The original article found on darkreading Read More
DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack
Multiple threat activity clusters with ties to North Korea (aka Democratic People’s Republic of Korea or DPRK) have been linked to attacks targeting organizations and […]
Japan Warns on Unauthorized Stock Trading via Stolen Credentials
Attackers are using credentials stolen via phishing websites that purport to be legitimate securities company homepages, duping victims and selling their stocks before they realize […]
Kubernetes Pods Are Inheriting Too Many Permissions
Scalable, effective — and best of all, free — securing Kubernetes workload identity cuts cyber-risk without adding infrastructure, according to new research from SANS. The […]

_Olekcii_Mach_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)