In 2025, employees are still using weak passwords. Instead of forcing an impossible change, security leaders are working around the problem. The original article found […]
Coyote, Maverick Banking Trojans Run Rampant in Brazil
South America’s largest country is notorious for banking malware attacks; Maverick self-terminates if its targeted user is based outside Brazil. The original article found on […]
Malicious npm Package with 206K Downloads Targeting GitHub Repositories to Steal Tokens
On Friday, November 7th, Veracode Threat Research discovered a dangerous typosquatting campaign targeting developers using GitHub Actions. The malicious npm package “@acitons/artifact” had accumulated over […]
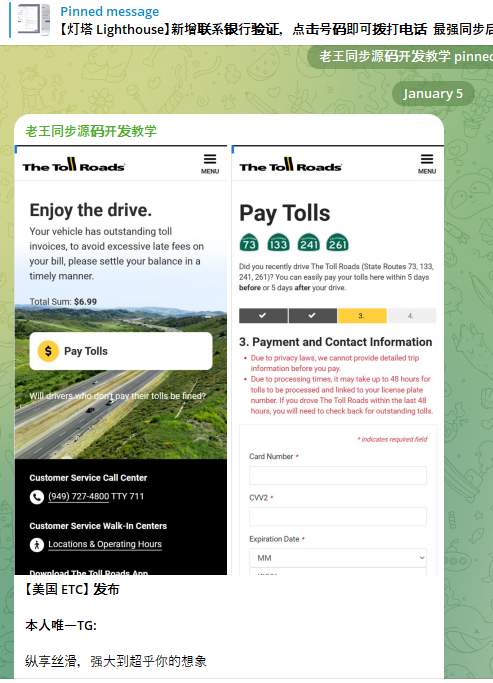
Phishing Emails Alert: How Spam Filters Can Steal Your Email Logins in an Instant
Cybercriminals have launched a sophisticated phishing campaign that exploits trust in internal security systems by spoofing email delivery notifications to appear as legitimate spam-filter alerts […]
Google Sues to Disrupt Chinese SMS Phishing Triad
Google is suing more than two dozen unnamed individuals allegedly involved in peddling a popular China-based mobile phishing service that helps scammers impersonate hundreds of […]
Fake Chrome Extension “Safery” Steals Ethereum Wallet Seed Phrases Using Sui Blockchain
Cybersecurity researchers have uncovered a malicious Chrome extension that poses as a legitimate Ethereum wallet but harbors functionality to exfiltrate users’ seed phrases. The name […]
OpenAI Sora 2 Vulnerability Allows Exposure of Hidden System Prompts from Audio Data
Security researchers have successfully extracted the system prompt from OpenAI’s Sora 2 video generation model by exploiting cross-modal vulnerabilities, with audio transcription proving to be […]
Hackers Infiltrate npm Registry with 43,000 Spam Packages, Linger for Nearly Two Years
Security researcher Paul McCarty has uncovered a massive coordinated spam campaign targeting the npm ecosystem. The IndonesianFoods worm, comprising over 43,000 malicious packages published across […]
Threat Actors Use JSON Storage for Hosting and Delivering Malware via Trojanized Code
A sophisticated campaign attributed to North Korean-aligned threat actors is weaponizing legitimate JSON storage services as an effective vector for deploying advanced malware to software […]
SmartApeSG Uses ClickFix to Deploy NetSupport RAT
The SmartApeSG campaign, also known as ZPHP and HANEYMANEY, continues to evolve its infection tactics, pivoting to ClickFix-style attack vectors. Security researchers have documented the […]