A sophisticated social engineering technique known as ClickFix has emerged, leveraging fake CAPTCHA verification processes to deceive users into executing malicious commands. This method exploits […]
Apache Tomcat Vulnerability (CVE-2025-24813) Exploited to Execute Code on Servers
A critical vulnerability in Apache Tomcat has been actively exploited by attackers to achieve remote code execution (RCE) on vulnerable servers. This vulnerability affects versions […]
TsarBot Android Malware Mimics 750 Banking & Finance Apps to Steal Credentials
A newly discovered Android banking malware named TsarBot is targeting over 750 applications globally, including banking, finance, cryptocurrency, and e-commerce platforms. Identified by Cyble Research […]
RESURGE Malware Exploits Ivanti Flaw with Rootkit and Web Shell Features
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has shed light on a new malware called RESURGE that has been deployed as part of exploitation […]
CISA Warns of ESURGE Malware Exploiting Ivanti RCE Vulnerability
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a Malware Analysis Report (MAR-25993211-r1.v1) detailing the exploitation of a critical vulnerability in Ivanti Connect Secure […]
Lotus Blossom APT Exploits WMI for Post-Exploitation Activities
The Lotus Blossom Advanced Persistent Threat (APT) group, also known as Lotus Panda, Billbug, and Spring Dragon, has intensified its cyberespionage efforts with new variants […]
RamiGPT – AI Tool To Escalate Privilege & Gain Root Access Within a Minute
A new AI-driven offensive security tool, RamiGPT, is known for its ability to autonomously escalate privileges and gain root access to vulnerable systems in under […]
Fake Snow White Movie Attacking Viewers Device With New Malware
Disney’s latest release, Snow White (2025), has turned into a cybersecurity crisis for unsuspecting users. With a disappointing IMDb rating of 1.6/10 and lackluster box […]
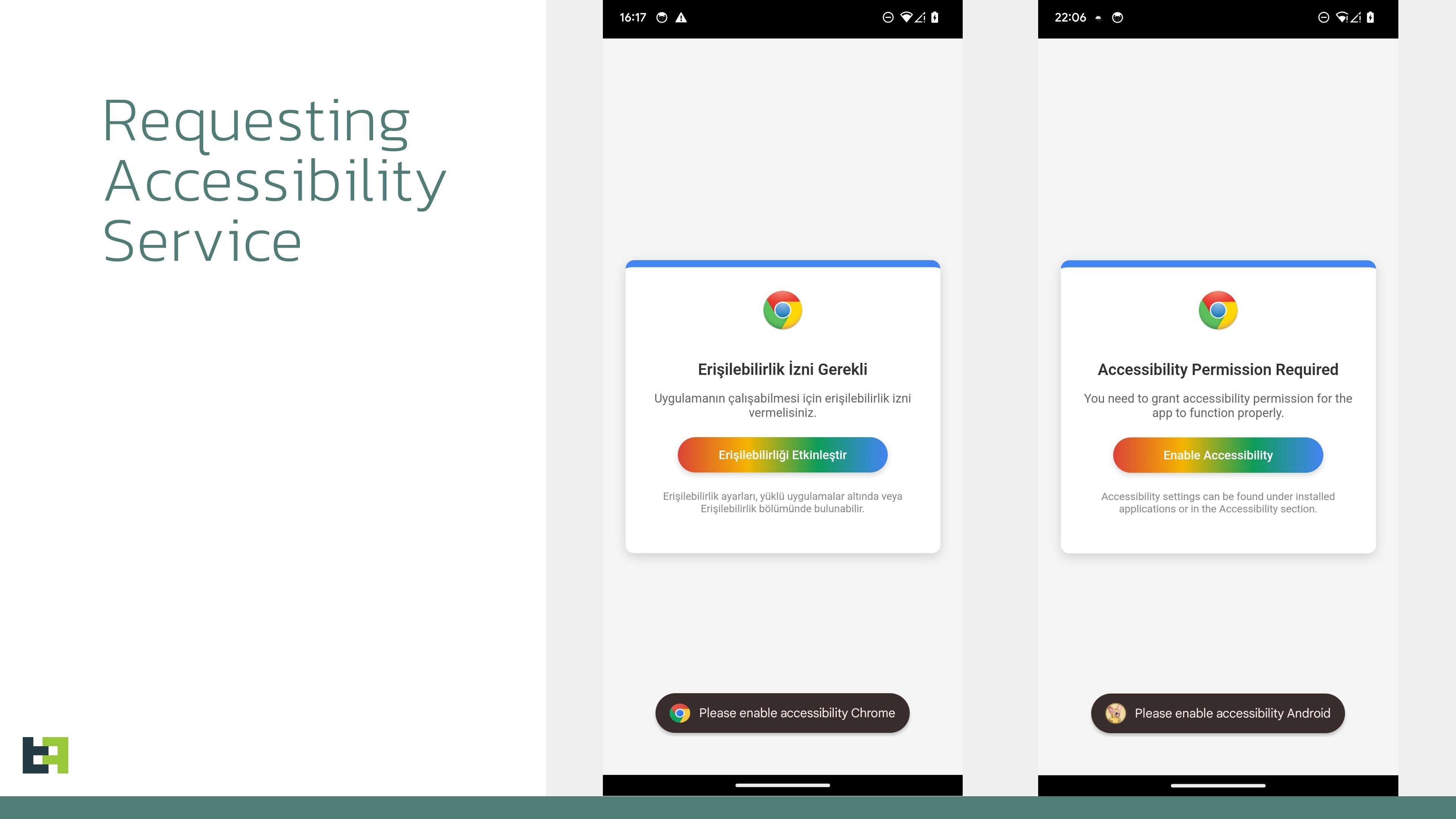
Crocodilus – A New Android Malware Remotely Control Your Android Devices
Researchers has identified a novel mobile banking Trojan, designated “Crocodilus,” marking a significant advancement in the evolution of Android-targeted malware. Unlike predecessors such as Anatsa, […]
Hackers Leveraging DNS MX Records To Dynamically Create Fake Logins Mimic as 100+ Brands
A sophisticated phishing operation has emerged that creatively leverages DNS mail exchange (MX) records to dynamically serve fake login pages tailored to victims’ email providers. […]




.webp)