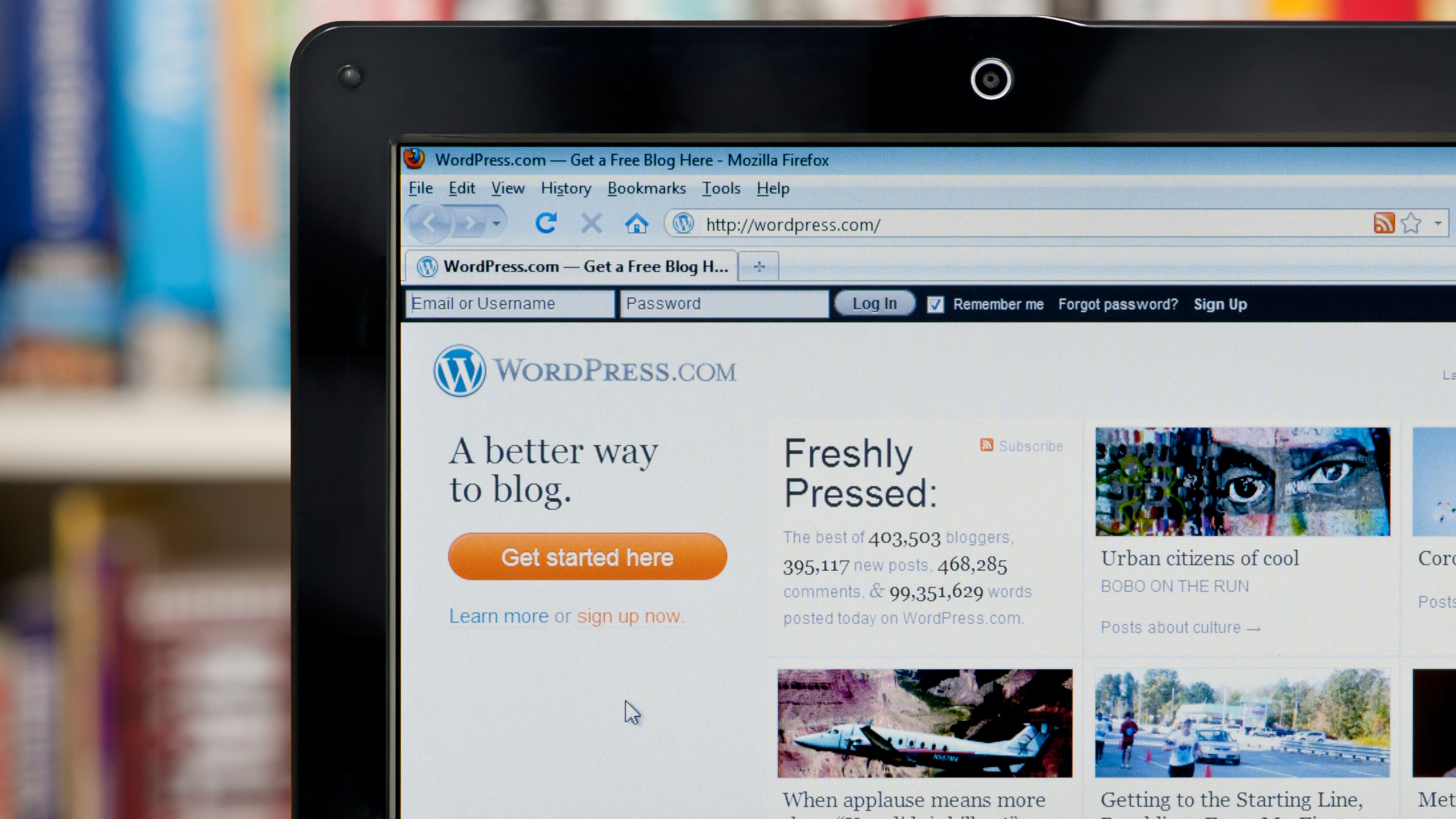
A massive cybercrime network known as “VexTrio” is using thousands of compromised WordPress sites to funnel traffic through a complex redirection scheme. The original article […]
Why It’s So Hard to Stop Rising Malicious TDS Traffic
Cybersecurity vendors say threat actors’ abuse of traffic distribution systems (TDS) is becoming more complex and sophisticated — and much harder to detect and block. […]
Ukraine Defense Sector Under Attack Via Dark Crystal RAT
The UNC-200 threat group, active since last summer, has been utilizing the Signal messaging app to social engineer targets into downloading an infostealing remote access […]
YouTube Game Cheats Spread Arcane Stealer Malware to Russian-Speaking Users
YouTube videos promoting game cheats are being used to deliver a previously undocumented stealer malware called Arcane likely targeting Russian-speaking users. “What’s intriguing about this […]
Microsoft Attributes Recent Outage of Outlook Web to Code Error in Recent Update
Microsoft experienced a widespread outage on March 19, 2025, affecting Outlook on the web services. The tech giant has attributed the issue to a problematic […]
RansomHub Affiliate Deploying New Custom Backdoor Dubbed ‘Betruger’ For Persistence
A RansomHub affiliate has been observed recently deploying a new custom backdoor named ‘Betruger’. This sophisticated malware, discovered on March 20, 2025, by the Symantec […]
New Steganographic Malware Exploits JPEG Files to Distribute Infostealers
A sophisticated malware campaign employing steganographic techniques has recently been identified, targeting users through seemingly innocent JPEG image files. The attack leverages hidden malicious code […]
Veeam and IBM Release Patches for High-Risk Flaws in Backup and AIX Systems
Veeam has released security updates to address a critical security flaw impacting its Backup & Replication software that could lead to remote code execution. The […]
HP Brings Quantum-Safe Encryption to Printers
HP’s 8000 Series enterprise and commercial printers, which include Color LaserJet Enterprise MFP 8801, Mono MFP 8601, and LaserJet Pro Mono SFP 8501, will feature […]
IBM AIX Vulnerability Let Attackers Execute Arbitrary Commands
Critical security vulnerabilities in IBM AIX operating systems could allow unauthorized remote attackers to execute arbitrary commands, potentially compromising the entire system. IBM has released […]