In a landmark development for cybersecurity infrastructure, Google’s Mandiant subsidiary has unveiled GoStringUngarbler – an open-source deobfuscation framework designed to neutralize advanced string encryption techniques […]
15 Best Patch Management Tools In 2025
Patch management tools are essential for maintaining the security and efficiency of IT systems in 2025. These tools automate the process of identifying, testing, and […]
60% of cybersecurity pros looking to change employers
Cybersecurity worker job satisfaction is mediocre with many staff actively considering a change. Only a third or respondents to an annual Cybersecurity Staff Compensation Benchmark […]
50 World’s Best Cyber Security Companies – 2025
Cybersecurity has transformed from a niche technical field into a critical business priority that shapes organizational strategies worldwide. As we navigate through 2025, the cybersecurity industry continues to […]
Android App With 220,000+ Downloads From Google Play Installs Banking Trojan
A sophisticated Android banking trojan campaign leveraging a malicious file manager application accumulated over 220,000 downloads on the Google Play Store before its removal. Dubbed […]
SecP0 Ransomware Group Threatens Organizations to Leak Vulnerability Details
A new ransomware group, SecP0, has emerged on the cybercrime landscape, adopting a novel and deeply concerning tactic: demanding ransom payments not for encrypted data, […]
Two Hackers Arrested for Stealing Taylor Swift Era Concert Tickets Worth $600k
In a sophisticated cybercrime operation targeting high-demand events, two individuals were arrested this week for allegedly orchestrating a $600,000 ticket theft scheme involving Taylor Swift’s […]
U.S. Charges 12 Chinese Nationals in State-Backed Hacking Operations
The U.S. Department of Justice (DoJ) has announced charges against 12 Chinese nationals for their alleged participation in a wide-ranging scheme designed to steal data […]
Bybit Hot Wallet Exploit for Malicious Transaction – Technical Analysis Released
Researchers uncovered one of the most technically sophisticated attacks in cryptocurrency history, exploiting Bybit’s Ethereum hot wallet infrastructure through a malicious proxy contract upgrade. The […]
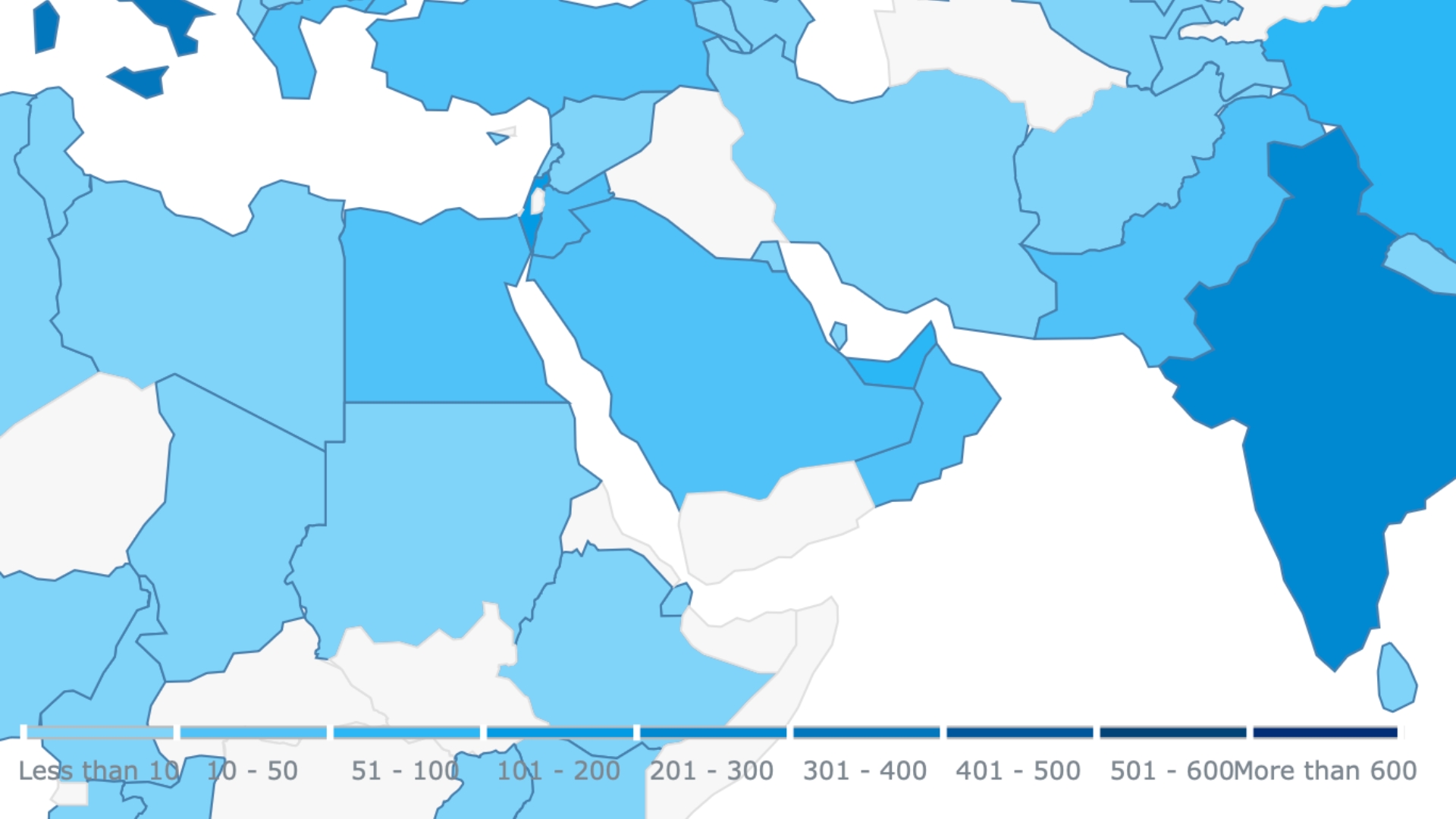
Ransomware Attacks Build Against Saudi Construction Firms
Cybercriminals are ramping up their efforts in the Kingdom and targeting more than just petroleum firms; now, they’re aiming for Middle East organizations in the […]

.webp)