Bug bounty programs remain a crucial component of cybersecurity strategies in 2025, offering organizations the ability to draw in help from a diverse pool of […]
Google Warns of PROMPTFLUX Malware That Uses Gemini API for Self-Rewriting Attacks
Cybersecurity researchers at Google Threat Intelligence Group (GTIG) have identified a significant shift in how threat actors are leveraging artificial intelligence in their operations. The […]
What past ERP mishaps can teach CISOs about security platformization
Research studies indicate that the average enterprise has between 40 and 80 separate security tools, a broad inventory that often leads to multiple security data […]
SonicWall Confirms State-Sponsored Hackers Behind September Cloud Backup Breach
SonicWall has formally implicated state-sponsored threat actors as behind the September security breach that led to the unauthorized exposure of firewall configuration backup files. “The […]
HackedGPT: New Vulnerabilities in GPT Models Allow Attackers to Launch 0-Click Attacks
Cybersecurity researchers at Tenable have uncovered a series of critical vulnerabilities in OpenAI’s ChatGPT that could allow malicious actors to steal private user data and […]
Gootloader Returns with a New ZIP File Tactic to Conceal Malicious Payloads
Cybersecurity researchers have discovered a resurgent Gootloader malware campaign employing sophisticated new evasion techniques that exploit ZIP archive manipulation to evade detection and analysis. Credit […]
2026 – nichts für schwache CI(S)O-Nerven
Aus Sicht von Forrester bleibt die Lage für IT-(Sicherheits-)Entscheider auch 2026 angespannt. Maya Lab /Shutterstock Keine Entwarnung für IT-(Sicherheits-)Entscheider: Die Analysten von Forrester gehen in […]
Google researchers detect first operational use of LLMs in active malware campaigns
Threat actors are now actively deploying AI-enabled malware in their operations. Google Threat Intelligence Group (GTIG) has identified cybercriminal use of “just-in-time” AI which employs […]
APT ‘Bronze Butler’ Exploits Zero-Day to Root Japan Orgs
A critical security issue in a popular endpoint manager (CVE-2025-61932) allowed Chinese state-sponsored attackers to backdoor Japanese businesses. The original article found on darkreading Read […]
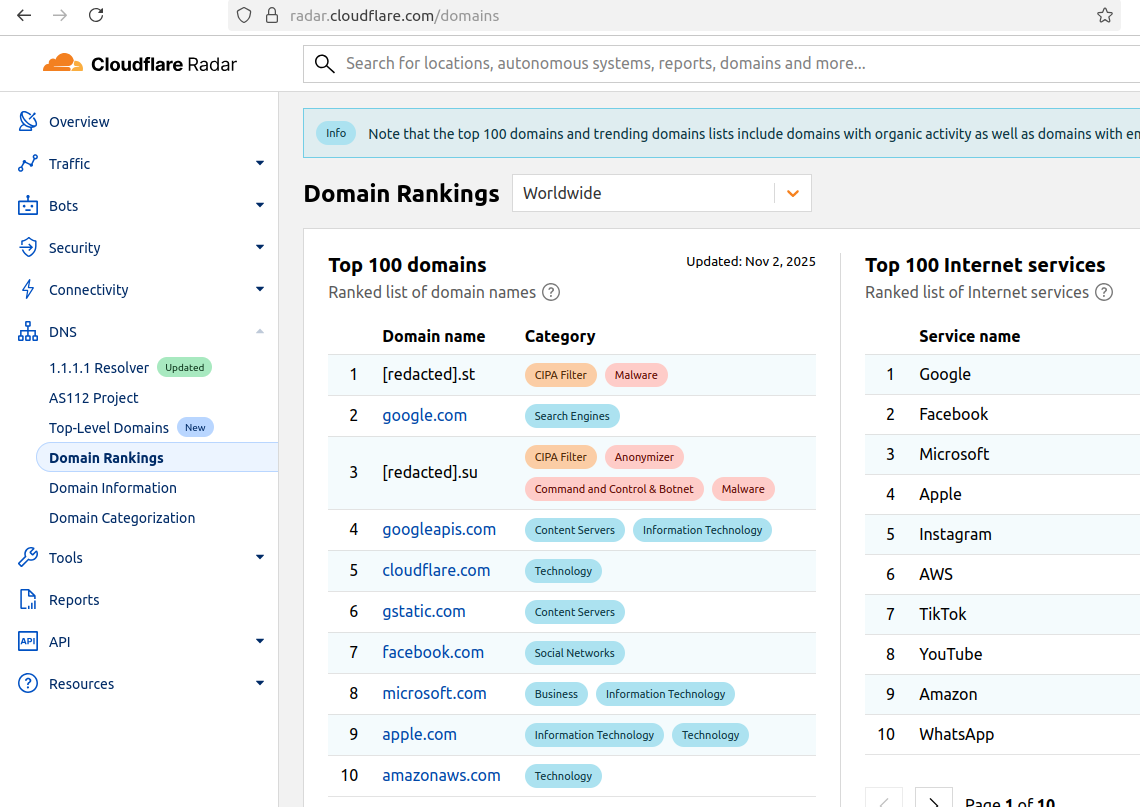
Cloudflare Scrubs Aisuru Botnet from Top Domains List
For the past week, domains associated with the massive Aisuru botnet have repeatedly usurped Amazon, Apple, Google and Microsoft in Cloudflare’s public ranking of the […]