As we move into 2025, the cybersecurity landscape continues evolving with significant incidents and trends that demand attention. Here’s a roundup of the top 5 […]
ISACA State of Privacy 2025: Briefing Document
Executive Summary The ISACA State of Privacy 2025 report, based on a survey conducted in September 2024, explores key trends in privacy staffing, operations, budgets, […]
Top 5 Cybersecurity News Articles for the Week of January 5, 2025
As we kick off 2025, the cybersecurity landscape is already presenting new challenges and developments that professionals need to be aware of. Here’s a roundup […]
Top 5 Cybersecurity News Articles for the Week of December 22, 2024
As we approach the end of 2024, the cybersecurity landscape has been marked by significant events and emerging trends that will shape the future of […]
How Nation-State Cybercriminals Target Enterprises
Nation-state cybercriminals represent one of the most sophisticated and dangerous threats to enterprises today. These attackers, often backed by government resources, are not only well-funded […]
Top 5 Cybersecurity News Articles for the Week of December 8, 2024
As we move further into December, the cybersecurity landscape remains dynamic, with new threats and insights emerging regularly. Here’s a roundup of the top 5 […]
Krispy Kreme Cyberattack: A Sweet Disruption
Last week, Krispy Kreme was in a sticky situation as the beloved doughnut chain experienced a significant cyberattack that disrupted its online operations. The incident, […]
Navigating the Future: AI Advancements and Cybersecurity Challenges in 2025
As we approach 2025, the tech landscape is poised for significant transformations, particularly in the realms of artificial intelligence (AI) and cybersecurity. With technological advancements […]
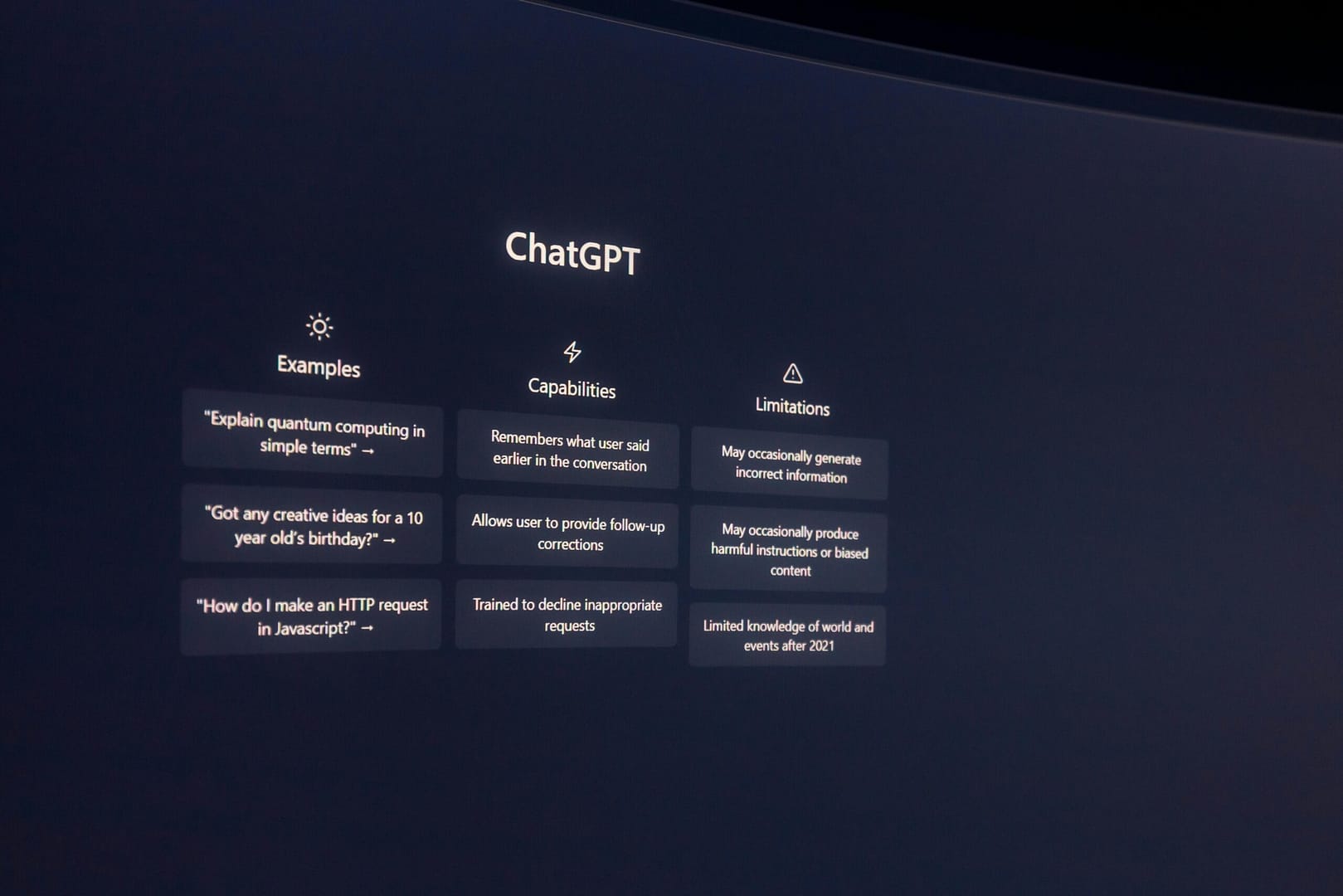
Exploring the Transformative Impact of ChatGPT on Industries and Cybersecurity
ChatGPT, a leading generative AI model, is revolutionizing industries by reshaping workflows, enhancing creativity, and addressing critical cybersecurity challenges. This innovation brings opportunities and risks, […]
The Resurgence of Skimmer Malware in E-Commerce: Protecting Your Checkout Pages
E-commerce platforms are once again in the crosshairs of cybercriminals with a newly identified credit card skimmer malware that specifically targets checkout pages. Known as […]